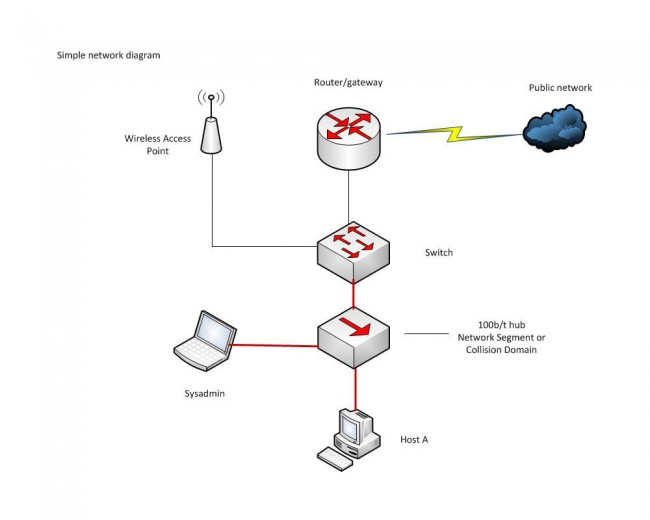
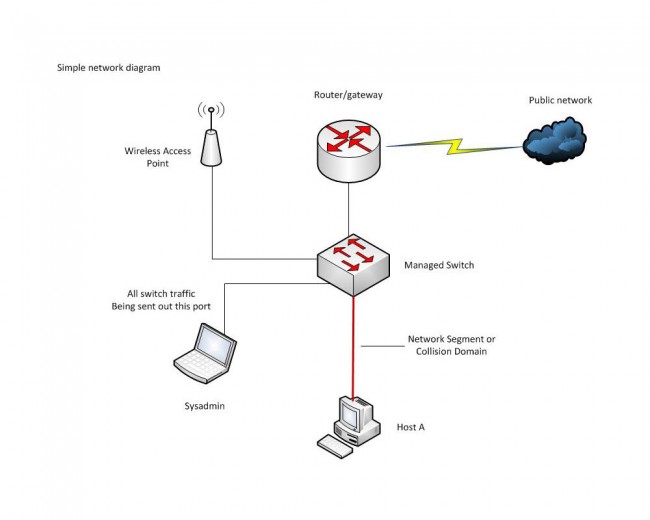
I have been working with GNS3 (Graphical Network Simulator) in some of my classes. It is a fine tool with which one can build simulated computer networks using various routers and switches. The software program itself is free, however, the Cisco IOS images are not included and must be found elsewhere due to copyright issues. This detail is a bit of a pain, but not too bad. Once the program is set up and the appropriate IOS images are loaded, the console functions exactly like whatever router is being simulated. This includes running whichever terminal program is preferred, e.g. hyperthermia, putty, or if using the Linux version, x-term, etc.
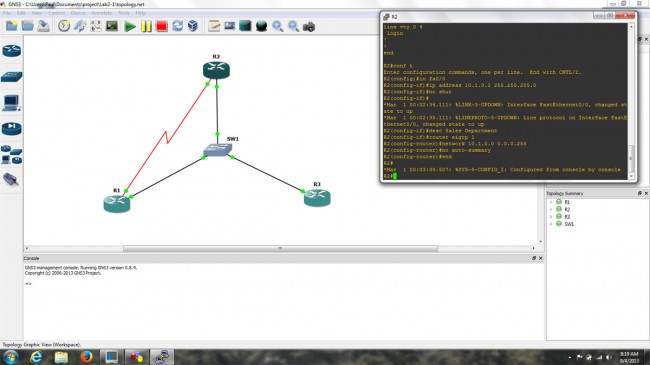
The advantages to this over something like Cisco’s Packet Tracer program are many. In Packet Tracer, certain functions are locked out and generally there is only one acceptable way to complete any given task. With GNS3, the IOS is fully functional, which means that experimentation and failure are available to play with. Failure is a great way to learn things in any hands-on environment. The advantage of virtual failure is that only you know about it.
For real-world applications, this means that router and switch configurations can be created, tested, and tuned ahead of time and then loaded into working devices, saving downtime and potentially handfuls of hair.
A few things about using GNS3, the PC idle tuning is required. Each instance of IOS assumes that the entire processor is available to use, thus starting several routers can work a PC’s processor to 100% and windows will never fully recover. Secondly, when starting each router, wait 10 to 20 seconds before starting another one. Again, this has to do with the way IOS uses processors. Also, to save time, store the IOS image as a decompressed file. This saves quite a bit of time on startup. Finally, do not forget to copy the running config to startup-config. Even though GNS3 says it is saving the router configs, it does not save the running config unless you issue the copy run start command, just like a real router.