Most broadcast facilities have an engineering department or service and an IT department or service which are separate. There is often a fuzzy line between what machines belong strictly to engineering and what belongs to IT. There are several different systems that have network interfaces but are not generally considered computers and fall squarely in the engineering department. These include such equipment as transmitters, satellite receivers, EAS machines, IP-based audio routers and audio consoles, and IP audio CODECS. In many cases, windows based automation systems and servers also fall under the responsibility of the engineering department.
As the recent incidents of network intrusions into vulnerable EAS machines show, after installation, steps must be taken to secure networked equipment from malicious or accidental intrusions. The aforementioned EAS intrusion was bad but it could have been much worse.
Anything with a network interface can be exploited either internally or externally and either by purpose or accident. The threat plan looks like this:
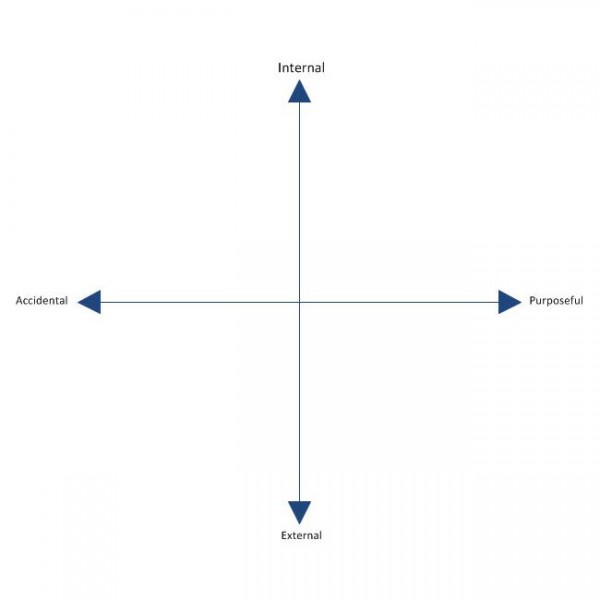
Every unauthorized network access incident falls somewhere on this plain. An unauthorized network intrusion can be as simple as somebody using the wrong computer and gaining access to back-end equipment. It can also be the hacker or cracker from a foreign country attempting to breach a firewall.
Basic network security falls into these categories:
- Physical security of machine or server room
- Security against internal accidental or malicious use
- Security against external intrusion
- Protection against malicious software exploitation
The first category is the easiest to understand. Physical security means securing the server room through locking doors and preventing crawl-over/under entries. Security cameras and monitoring are also a part of physical security. Something that is often neglected is extended networks that bridge to transmitter sites. Non-maned off site facilities that have network access are vulnerable points if multiple clients or tower tenants have access to the same room. Locked equipment racks and video cameras are two ways to secure non-maned transmitter sites. Also, when using good quality, managed switches at transmitter sites, switch port security features can be enabled, and unused switch ports shut down.
Accidental or malicious internal intrusions can be reduced or eliminated with proper password policies. The first and most important password policy is to always change the default password. There are lists of default routers and switch passwords available online. The default passwords for EAS machines and other equipment is published in owner’s manuals and most broadcast engineers know them by heart. Always change the default password, if you do nothing else, do this.

Other password policies include such things as minimum password length, requiring special characters, numbers and both upper and lower case letters. Even taking those steps, passwords are still vulnerable to dictionary attacks. To prevent a dictionary attack, the login attempts should be limited to five or so with a thirty minute freeze out after the attempt limit is reached.
External intrusion can come from a number of different sources. Unsecured WIFI is the easiest way to gain access to a network. Always secure WIFI with WPA or WPA2 AES encrypted pre-shared key. This will keep all but the most determined intruders out. Other external threats can come from man in the middle attacks. IP bridges and WIFI must always be encrypted.
External attacks can also come over the wired network. Most small routers have default network and password settings. I have started moving away from using 192.168 internal networks. Router firewalls and personal software firewalls are effective but not foolproof. Software updates need to be performed regularly to be effective. One recently discovered exploit is UPnP, which is enabled on many home and small office routers. UPnP (Universal Plug-n-Play) SSDP (Simple Service Discovery Protocol) can be exploited of exposed to the public network side of the router. ShieldsUP! by Gibson Research Corporation is a good evaluation tool for router exploits, leaks and phone homes. They also have links to podcasts and youtube videos.
Disabling unused features on routers is a good security policy. Features such as DHCP, DNS, SNMP, CDP, HTTP server, FTP server etc are all vulnerable to exploitation of one form or another. Turning off those protocols that are not in use will eliminate at least a portion of those threats.
Finally, worms, bots, viruses and other malicious software can come from anywhere. Even reputable websites now have drive-bys in linked advertizing banners. Non-windows operating systems are less vulnerable to such programs, but not immune. All windows machines and servers that are in anyway connected to the internet need to have updated antivirus software. Keyloggers can steal passwords and send them to bad places where people have nefarious intent.
There are entire books, standards and upper level classes taught on network security. This less than 1,000 word article barely brushes the surface, as the titles says, these are but a few very basic ways to implement a security policy. It is important for technical managers and engineers to learn about, understand and implement security policies in broadcast facilities or suffer the consequences of complacency.




I think a related concept here can be summarized with “be careful what you put online”
Recently I was watching a transmitter site tour video on youtube. I love the opportunity to see different radio facilities from the comfort of my living room. However, in this particular video, the cameraman panned over rack that contained among other things, a remote control unit for the facility. I stopped the video and was able to clearly see the unit make and model as well as the box’s phone number neatly labelled on the front.
About two seconds on Google got me the operating manual for remote control unit. All that was left was to give it a call and see if the default passcode had been changed or was trivial, then onto all sorts of mischief.
Did I call it? No, of course not. I wouldn’t want that done to me. But here was an attack vector that I’m guessing the person holding the camera had no idea they were revealing.
Please do post pictures and videos of studio and transmitter facilities, they are a lot of fun to watch. But also be careful to not unwittingly reveal sensitive information, like phone numbers, IP addresses, even personal information seen around studio and office desks.
Matt, you bring up a good point. Always check those pictures before they go up on facebook or a website. I make sure to remove phone numbers, personal license plates, IP addresses, and sometimes call letters or other identifying information from pictures and videos before they go up.
Also, I am sure that there are more than a few dial in remote controls that still have their default security codes.
And please be aware that writing down a password on a device is not a good idea in ANY case. Store them at a save place, where visitors, sub-contractors and thiefs can’t find them.
Internal IP-Adresses are not a big problem, anyone having physical access to your network (after breaking firewalls, wifi protection, putting a cable into a switch port) can easily figure out which IP-range/subnet is in use within seconds. But of course, it is better to store them at a safe place too, making it not too easy for untrained victims.
My personal recommendation is that you should put any device that’s directly or indirectly connected to your airchain *on a physically separate LAN*, with different colored cable everywhere (including jack faces and drop cords) – usually red, unless you have to use red for the public side of your router firewall, which can easily be orange…
and then put a second firewall between that production LAN and the main firewall connection, with *no connections allowed in either direction* by default; open only the holes you *need to* and *know about*.
Matt, are you crazy, you want Paul to not post any more transmitter site pictures????
@Matt: It doesn’t even have to be online to be considered dangerous. I remember some years ago a newspaper piece spotlighting an on-air personality. The rather sizable photo was with the jock sitting in the main studio’s console. Only slightly out of focus was their emergency sheet with staff phone numbers and cell/pager codes! I never noticed if their Burke code was on the sheet but I wouldn’t have been surprised.
I have to agree with Baylink on having separate LANs for both public/office use and for on-air support equipment. The last facility I was at had their Enco and studio machines totally divorced from their office network and it worked well.
Another thing about passwords is that they should be changed anytime people who know the passwords leave your employer. And I’ve always changed passwords to major systems every 90 days as well. Sure, it’s a PITA but that’s easier than standing in front of the Big Boss explaining why you got hacked, knocked off the air or had something else happen. And don’t forget to change the combinations on any door locks that use them.