Wireshark is a packet protocol analyzer that is free for download and runs on Windows, Linux, BSD, OS X, and Solaris. In the evolving broadcasting studio, computer networks are the backbone of the facility. Not just on the office side of the house, but also on the broadcast origination side as well. Today, almost everyone uses some type of computer automation system running on a network. In addition, new technologies such as AoIP consoles, VoIP phone systems, audio and video routing, remote control, off-site monitoring, audio processing, etc continue to develop. Because of this, more and more broadcast engineering work is falling into the computer and networking realm.
Like anything else, networks can fail. Failure modes can originate from both the physical side, e.g. wiring, connectors, patch bays, network interface cards or the software/protocol side. Being able to diagnose problems quickly and take remedial action is important. On the networking side, if a physical problem has been ruled out, then the problem exists with a protocol. That is where Wireshark becomes useful; it takes the guesswork out of networking protocol troubleshooting.
Wireshark packet protocol analyzer has the following features (from their website):
- Deep inspection of hundreds of protocols, more are in development
- Live capture and offline analysis
- Standard three-pane packet browser
- Versions available for Windows, Linux, OS X, Solaris, FreeBSD, NetBSD, and other OS
- Captured network data can be browsed via a GUI, or via the TTY-mode TShark utility
- Filtering by protocol, IP address, MAC address, frame type, sequence number, etc
- VoIP analysis
- Read/write many different capture file formats: tcpdump (libpcap), Pcap NG, Catapult DCT2000, Cisco Secure IDS iplog, Microsoft Network Monitor, Network General Sniffer® (compressed and uncompressed), Sniffer® Pro, and NetXray®, Network Instruments Observer, NetScreen snoop, Novell LANalyzer, RADCOM WAN/LAN Analyzer, Shomiti/Finisar Surveyor, Tektronix K12xx, Visual Networks Visual UpTime, WildPackets EtherPeek/TokenPeek/AiroPeek, and others
- Capture files compressed with gzip can be decompressed on the fly
- Live data can be read from Ethernet, IEEE 802.11, PPP/HDLC, ATM, Bluetooth, USB, Token Ring, Frame Relay, FDDI, and others (depending on your platform)
- Decryption support for many protocols, including IPsec, ISAKMP, Kerberos, SNMPv3, SSL/TLS, WEP, and WPA/WPA2
- Coloring rules can be applied to the packet list for quick, intuitive analysis
- Output can be exported to XML, PostScript®, CSV, or plain text
A few things to keep in mind with the physical connection. Connecting a computer to a switch port will establish a collision domain between the switch port and the computer which is also called a network segment. The computer NIC will see all traffic on that collision domain and all broadcast traffic on the network or sub-network that the switch is attached to. If there is a suspected problem with a particular network segment, the Wireshark computer needs to join that collision domain.
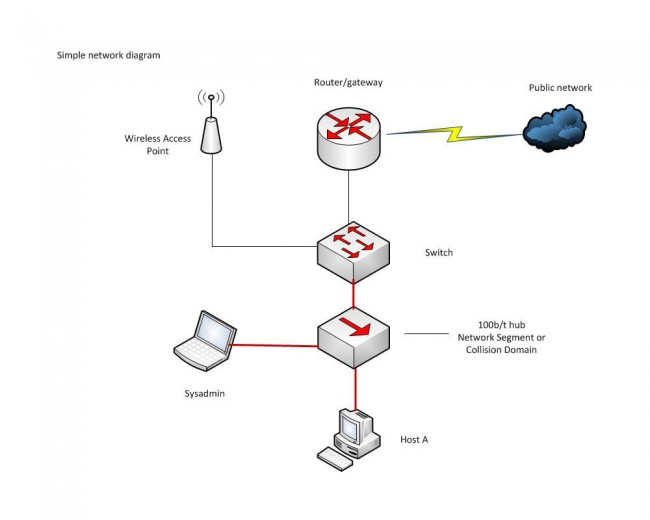
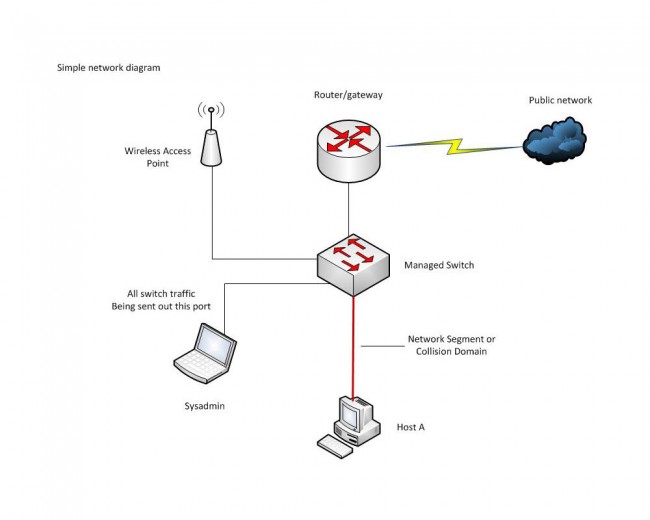
This can be done most simply by installing Wireshark on the host in that domain. Alternatively, a hub can be used to add another host to the collision domain. Or, if it is a managed switch, there may be a provision to send all traffic on the switch out of one designated port. This is called ‘port mirroring’, ‘port monitoring’, ‘Roving Analysis’ (3Com), or ‘Switched Port Analyzer’ or ‘SPAN’ (Cisco).
A quick tutorial on what to look for when using Wireshark, Part A:
Part B:
And briefly, that is how it is done. There are many more videos on youtube and elsewhere if interested in learning more.





Protip: keep your protocol dissectors up to date; they’re known to occasionally turn up with bugs, and if you’re running in realtime, you’re probably root/administrator… in which case that’s bad.
Wireshark is an excellent tool for what it does, but like all software-based protocol analyzers it is limited by the NIC in the system in which it is installed. It is my understanding that all consumer-grade NIC’s still filter out packets regardless of whether they are set to promiscuous mode. The traffic accepted by the NIC is governed by the NDIS miniport driver which in common NIC’s installed in most laptops is designed to keep certain traffic from passing regardless. I’m interested in hearing if anybody has heard of a relatively low-cost NIC that will truly pass all traffic in promiscuous mode. The alternative is to step up to a hardware-based protocol analyzer which are mucho bucks and out of my reach.