With the spate of ransomware and crypto virus attacks on automation systems, perhaps a quick review of network security is in order:
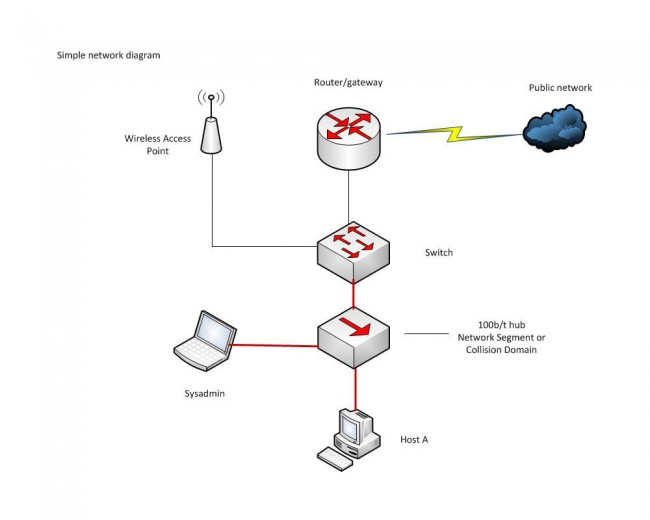
- Isolate the automation system on a separate network from the general office network and do not allow internet access on the automation system’s workstations or servers.
- Use a separate switch for all automation network connections.
- install a small router between the automation network and the office network. On the router, the WAN port faces outward toward the office network, making the WAN port non-pingable. Grant access from the office network for certain users; e.g. traffic, music director, etc via access lists. Open up a few ports for VNC or RDP on the router so technicians can remotely access machines to do maintenance and troubleshooting.
- Use supported and up-to-date operating systems.
- Use separate admin and user accounts, make sure that admin rights are removed from user accounts, and keep machines logged in as users. This ensures that some errant DJ or other person does not install any unauthorized programs.
- Install and keep up to date with a good antivirus program.
- Back up the data and test the backups.
The office network is more vulnerable because of the human element. Internet access is required, of course. Click on a pop-up, sure! Hey, that photograph has a funny file extension, lets’s open it and see what it is. I never heard of this person before, but look, they sent me an executable!
Much of the office network security will rely on the quality of the router connected to the internet and the antivirus software installed. Of course, the network users have a good deal of responsibility also.


Thank you Paul for the reminder! This newbie needs all the help he can get 🙂
Would you call TeamViewer as secure as VNC/RDP? That’s my remote access at the moment… and because I am running an internet station, my automation by default is connected to the Internet (though through a hardware option, not software encoder).
In addition to backups (most folks think of backups as the data and such) – I’d recommend having an image of the boot and software partitions of each computer in the automation system. If you’re looking for an open-source system to do this, have a look at setting up a FOG server. Otherwise there are other imaging options out there. Then in the event that automation system does get compromised to the point of a full reinstall, you’ve got a base image with software to start from, then it is a matter of restoring the data from the backup.
The weak point is probably the production machine in a lot of setups as it needs to access email, web and FTP sites AND be able to talk to the on-air servers.
I haven’t come up with a 100% solution for that one yet.
Minimal permissions, \\unc\ to the on-air machines instead of mapped drives and several fingers crossed….
Get rid of any log-in drive mapping to the automation.
Useful list – I’d add use linux computers/servers wherever you can – but automation/traffic/scheduling are Windows world.