I little bit of local awesomeness from the Putnam County Sheriff’s Department:
A Patterson (NY) man was committed to the Putnam County Jail in lieu of bail in connection with three separate thefts of copper fixtures from cell communications towers in Patterson and Kent.
The rest can be read here: Man charged with stealing copper from cellphone tower sites
I once got into an argument with my boss about transmitter site security cameras. His attitude was “what difference does it make, nobody will do anything about it anyway.” Clearly, if the police have something to go on, they will take action. I know that several E911 sites in Dutchess and Ulster counties have been victims of copper theft as well.
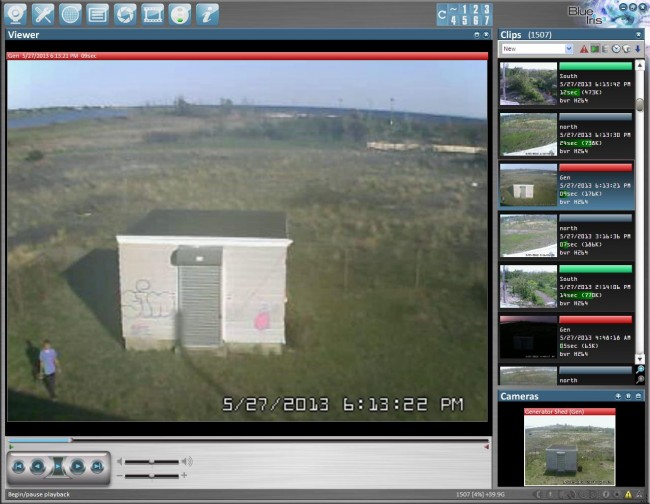
IP security cameras are inexpensive and fairly reliable, provided you keep them out of the direct elements. We have dozens of old Windows XP computers floating around which, with the addition of a software package like Blue Iris, can be repurposed as a record and save system. The advantage of Blue Iris is the record on motion. The cameras do not need to be monitored continuously; if something happens, go back and look at the stored video.
The old Windows XP boxes do not need to be connected to the outside world unless one wants to look at the security system from the studio or home. Alternatively, if one is Linux savvy, something like Zoneminder or Xeoma look like full featured video surveillance software packages. I have not fooled around with these yet, but perhaps when I have some spare time…
The point is, for not too much money, a full-featured video surveillance system can be installed at remote transmitter sites to keep track of comings and goings. If enough idiots get busted for stealing copper, perhaps it will stop (or at least slow down).