As more and more broadcast facilities are moving toward IP data for all types of data transfer including digitized audio, video, telephony, documents, email, applications, and programs. Managing an IP network is becoming more and more important. In most broadcast facilities, Ethernet-based IP networks have been the normal operating infrastructure for email, printing, file sharing, common programs, file storage, and other office functions for many years. Either directly or indirectly, most broadcast engineers have some degree of experience with networking.
With many more IP-based audio consoles, routing systems, STL’s and other equipment coming online, understanding IP networking is becoming a critical skill set. Eventually, all distribution of content will transition to IP-based systems and the current network of terrestrial broadcast transmitters will be switched off.
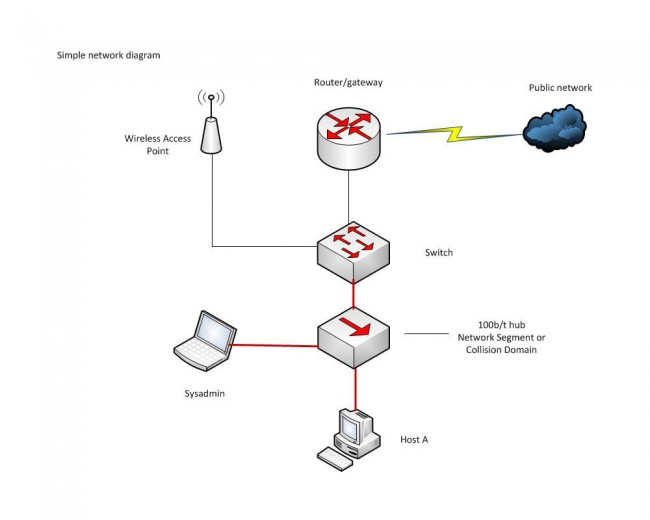
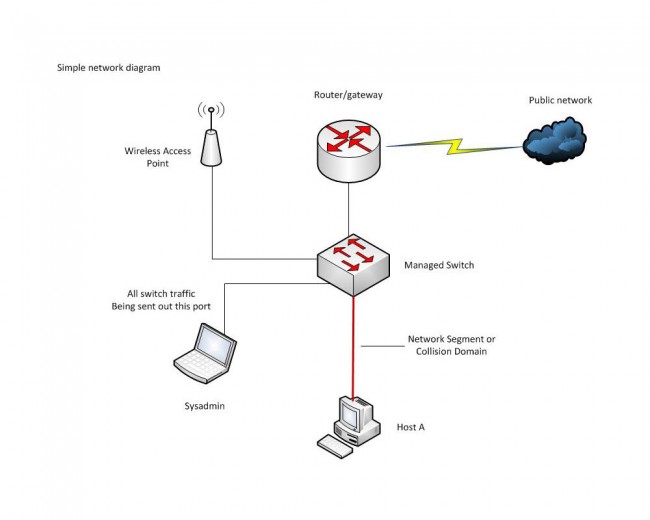
The difference between an ordinary office network and an AoIP (Audio over IP) or VoIP network is transfer consistency. In an office network, data transfer is generally bursty; somebody moves a file or requests an HTTP page, etc. Data is transferred quickly from point A to point B, then the network goes back to its mostly quiescent state. In the AoIP environment, the data transfer is steady state and the data volume is high. That is to say, once a session is started, it is expected to say active 24/7 for the foreseeable future. In this situation, any small error or design flaw, which may not be noticed on an office network can cause great problems on an AoIP network. The absolute worst kind of problem is intermittent failure.
Monitoring and analyzing data flow on a network can be a critical part of troubleshooting and network system administration. Data flow analysis can discover and pinpoint problems such as:
- Design flaws, infrastructure bottlenecks and data choke points
- Worms, viruses, and other malware
- Abusive or unauthorized use
- Quality of Service (QoS) issues
Cisco defines flow as the following:
A unidirectional stream of packets between a given source and destination—both defined by a network-layer IP address and transport-layer source and destination port numbers. Specifically, a flow is identified as the combination of the following seven key fields:
- Source IP address
- Destination IP address
- Source port number
- Destination port number
- Layer 3 protocol type
- ToS byte
- Input logical interface
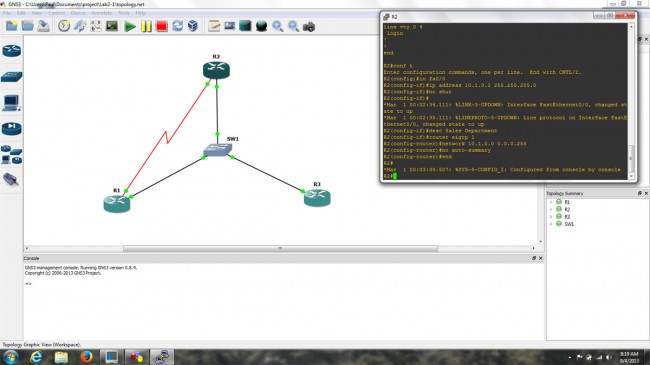
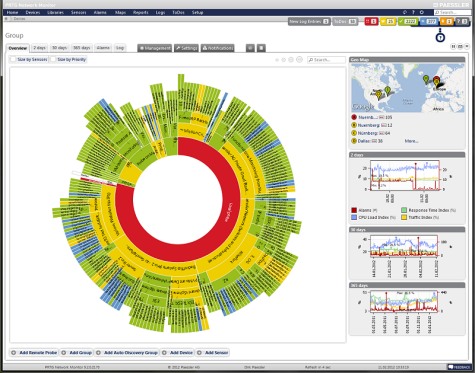
Packet sniffers such as Wire Shark can do this, but there are far better and easier ways to look at data flow. Network monitoring tools such as Paessler PRTG can give great insight as to what is going on with a network. PRTG uses SNMP (Simple Network Management Protocol) on a host machine to run the server core and at least one other host to be used as a sensor. There are instructions on how to run it as a virtual machine on a windows server, which would be the proper way to implement the server, in my opinion.
For small to medium installations, the freeware version may be all that is needed. For larger networks and major market installations, one of the lower-cost paid versions may be required.