Most broadcast facilities have an engineering department or service and an IT department or service which are separate. There is often a fuzzy line between what machines belong strictly to engineering and what belongs to IT. There are several different systems that have network interfaces but are not generally considered computers and fall squarely in the engineering department. These include such equipment as transmitters, satellite receivers, EAS machines, IP-based audio routers and audio consoles, and IP audio CODECS. In many cases, windows based automation systems and servers also fall under the responsibility of the engineering department.
As the recent incidents of network intrusions into vulnerable EAS machines show, after installation, steps must be taken to secure networked equipment from malicious or accidental intrusions. The aforementioned EAS intrusion was bad but it could have been much worse.
Anything with a network interface can be exploited either internally or externally and either by purpose or accident. The threat plan looks like this:
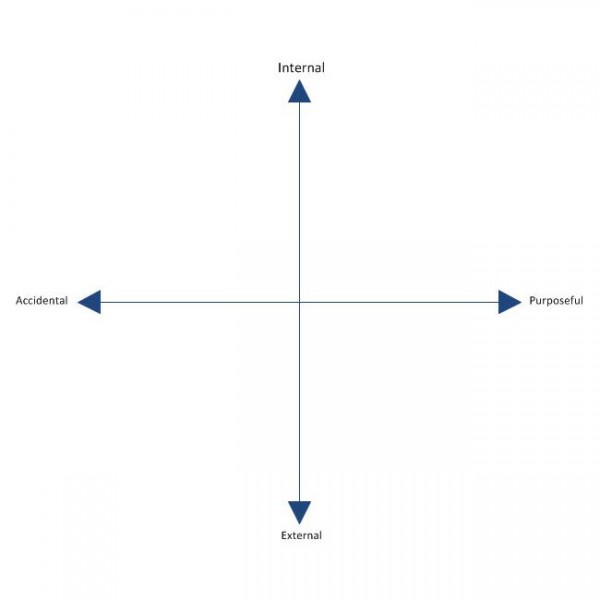
Every unauthorized network access incident falls somewhere on this plain. An unauthorized network intrusion can be as simple as somebody using the wrong computer and gaining access to back-end equipment. It can also be the hacker or cracker from a foreign country attempting to breach a firewall.
Basic network security falls into these categories:
- Physical security of machine or server room
- Security against internal accidental or malicious use
- Security against external intrusion
- Protection against malicious software exploitation
The first category is the easiest to understand. Physical security means securing the server room through locking doors and preventing crawl-over/under entries. Security cameras and monitoring are also a part of physical security. Something that is often neglected is extended networks that bridge to transmitter sites. Non-maned off site facilities that have network access are vulnerable points if multiple clients or tower tenants have access to the same room. Locked equipment racks and video cameras are two ways to secure non-maned transmitter sites. Also, when using good quality, managed switches at transmitter sites, switch port security features can be enabled, and unused switch ports shut down.
Accidental or malicious internal intrusions can be reduced or eliminated with proper password policies. The first and most important password policy is to always change the default password. There are lists of default routers and switch passwords available online. The default passwords for EAS machines and other equipment is published in owner’s manuals and most broadcast engineers know them by heart. Always change the default password, if you do nothing else, do this.

Other password policies include such things as minimum password length, requiring special characters, numbers and both upper and lower case letters. Even taking those steps, passwords are still vulnerable to dictionary attacks. To prevent a dictionary attack, the login attempts should be limited to five or so with a thirty minute freeze out after the attempt limit is reached.
External intrusion can come from a number of different sources. Unsecured WIFI is the easiest way to gain access to a network. Always secure WIFI with WPA or WPA2 AES encrypted pre-shared key. This will keep all but the most determined intruders out. Other external threats can come from man in the middle attacks. IP bridges and WIFI must always be encrypted.
External attacks can also come over the wired network. Most small routers have default network and password settings. I have started moving away from using 192.168 internal networks. Router firewalls and personal software firewalls are effective but not foolproof. Software updates need to be performed regularly to be effective. One recently discovered exploit is UPnP, which is enabled on many home and small office routers. UPnP (Universal Plug-n-Play) SSDP (Simple Service Discovery Protocol) can be exploited of exposed to the public network side of the router. ShieldsUP! by Gibson Research Corporation is a good evaluation tool for router exploits, leaks and phone homes. They also have links to podcasts and youtube videos.
Disabling unused features on routers is a good security policy. Features such as DHCP, DNS, SNMP, CDP, HTTP server, FTP server etc are all vulnerable to exploitation of one form or another. Turning off those protocols that are not in use will eliminate at least a portion of those threats.
Finally, worms, bots, viruses and other malicious software can come from anywhere. Even reputable websites now have drive-bys in linked advertizing banners. Non-windows operating systems are less vulnerable to such programs, but not immune. All windows machines and servers that are in anyway connected to the internet need to have updated antivirus software. Keyloggers can steal passwords and send them to bad places where people have nefarious intent.
There are entire books, standards and upper level classes taught on network security. This less than 1,000 word article barely brushes the surface, as the titles says, these are but a few very basic ways to implement a security policy. It is important for technical managers and engineers to learn about, understand and implement security policies in broadcast facilities or suffer the consequences of complacency.