Another trove of surveillance documents reveals some interesting technical aspects of spying in the modern age:
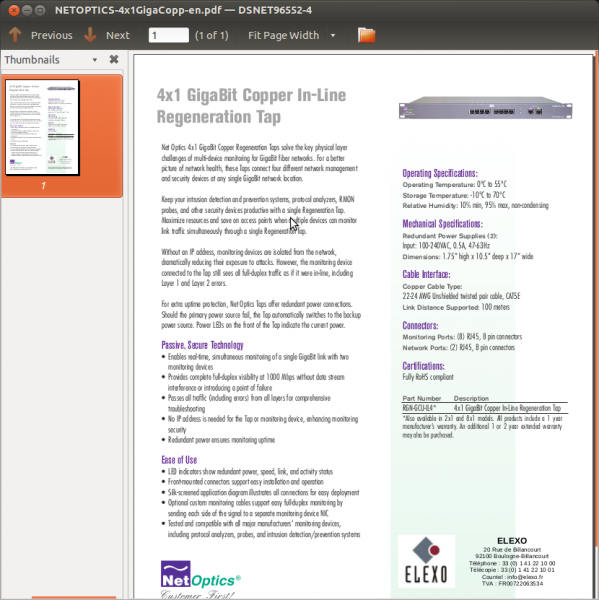
What we have here is a copper wiretap. This allows some telco or ISP to split an ethernet feed, and send one output on its merry way, while the other output goes to? If not interception and collection, I don’t rightly know what else this device is designed for.
There are many many more like this on the WikiLeaks website. Have any doubts about how deep the internet surveillance goes? Spend a few minutes poking around, it is an eye-opening experience.




While I’m sure many of these are used for purposes I might not think are appropriate (and/or legal), they do provide a way to debug point to point high speed ‘net connections between devices. We used to do this routinely w/ tools like Wireshark by inserting a simple (shared) hub when 10BT was the common connection method. With switched connections that no longer works and a “tap” (or a mirrored connection does.)
A simple search turns up many manufacturers of regen taps and plenty of less expensive devices that will mirror the contents of one port to another for packet capture.
Dale, Yes these devices are useful for many different things, however, the marketing in many of the brochures is targeting the surveillance market.
You do not need a hub or a special device to monitor or capture switched connections. Some Linux tools claim to be able to do that, too (e.g. http://en.wikipedia.org/wiki/Ettercap_%28computing%29). Technically, that isn’t really something new. It’s the sound that makes the music.
Hey Paul, my NRV buddy. Pleasant greetings to you my friend. I agree, this is sn interesting article. Last week I talked to an active duty Marine about AMVER. I told him about how we copied those reports via Morse Code and sent to New York in record message format. So, I searched the web for YouTube videos of someone copying AMVERs (or OBS) but, thus far haven’t found any; however, I found your site where you talked about our station, NRV. I did a great write-up. I too miss those days and that work. It was truly exciting and esoteric.
Just a quick note to say hello. I look forward to hearing from you.
73s
-XL
XL, always good to hear from an old shipmate. I’ll shoot you a email off line. PT
ARP poisoning is detectable and also, by definition, interferes with the operation of the network. In the legitimate “IDS” use this lets the IDS machine listen while keeping it isolated from 2-way communication with the network to avoid compromise.
Equally useful for nefarious purposes but Large Important Networks have plenty of demand just for the in-house role (think banks and Fortune 500s, for instance). At which point, once something suspicious is detected, it’s probably getting forwarded to law enforcement anyway.